How to build security into your software? It’s always simple to find examples where things gone wrong. Where security was compromised and things did not work out as the software authors envisioned.
As always there are new concepts and operating systems being implemented.
A particularly interesting example of security software design can be observed here:
Fuchsia is an open source capability-based operating system currently being developed by Google.
In contrast to prior Google-developed operating systems such as Chrome OS and Android, which are based on the Linux kernel, Fuchsia is based on a new microkernel called Zircon. The name Zircon refers to the mineral of the same name.
Google Fuchsia
So you now know what Fuchsia is. Now on to the actual example. For this we have to take a look into the developer documentation of Zircon:
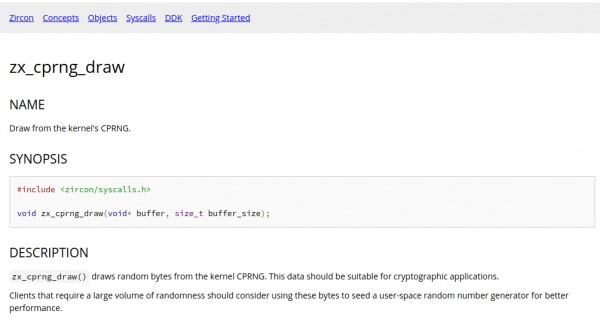
So this describes a method to get random numbers from the systems cryptocraphically-secure-random-number-generator (CPRNG). It takes a pointer to a memory location as a parameter.
Now. What’s secure about that? It’s the behaviour of the method when it is encountering an unsecure situation:
It’ll kill the calling process when the pointer is not valid.